What Does Coverage Mean for Digital Risks? Digital risk protection (DRP) refers to the “proactive defense of business assets against the threats they face.” This definition starts off with the notion of proactive defense which translates to concrete actions taken … Read More
Digital Risk Protection

What risks do unreported data breaches pose for your business?
What risks do unreported data breaches pose for your business? A database of 34 million user account records that were stolen from seventeen companies in 2020 is now for sale on a forum, Bleeping Computer reports. The dump has generated … Read More

Why digital risk protection is vital to protect data privacy in enterprise security
Why digital risk protection is vital to protect data privacy in enterprise security Privacy concerns have lately gained some serious momentum, as Daniel Therrien, Canada’s Privacy Commissioner, has warned that existing laws are behind international standards. This stalling appears to … Read More

Webinar Replay: State of the Cryptomarkets
Winners and Losers From the Shut Down of Empire Market David Hétu, Chief Research Office at Flare Systems investigated and presented the state of the cryptomarkets since one of the biggest illicit market shut down, Empire Market. Replay the webinar … Read More
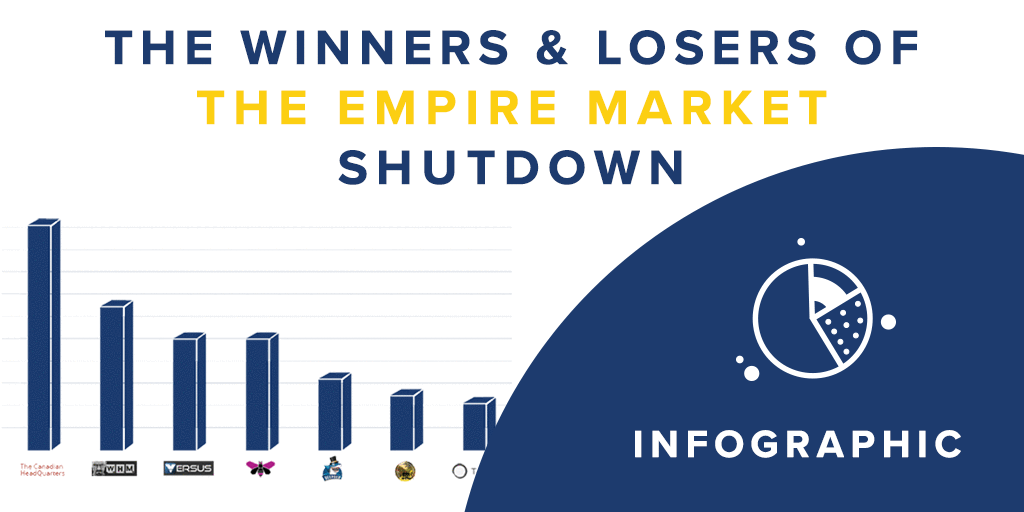
The Winners and Losers of the Empire Market Shutdown
Exit Scam Model of Empire Market In this infographic, we present how the shutdown of the most-trafficked dark web marketplace occured, the aftermath for the malicious actors and what we should expect next from the underground net threats. The exit … Read More
Hacker Contracts: The Economy Behind Illicit Markets
Hacker Contracts: The Economy Behind Illicit Markets Malicious actors often rely on each other to launch attacks. A carding ring that was recently dismantled by Russian authorities, for example, led to the arrest of 25 individuals who were working together. … Read More
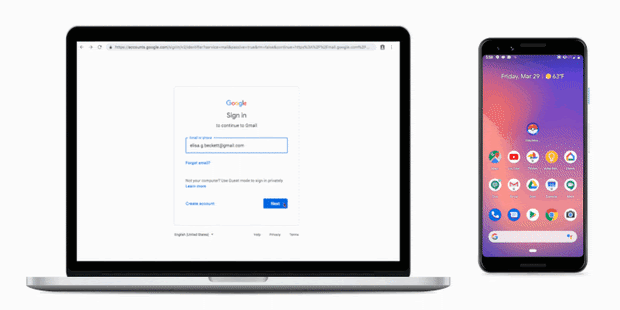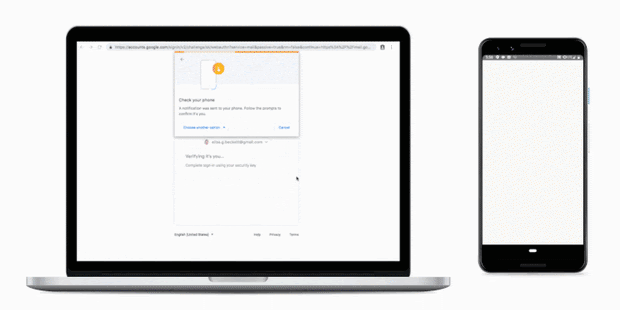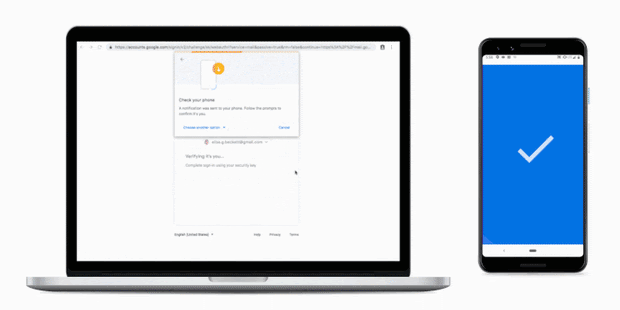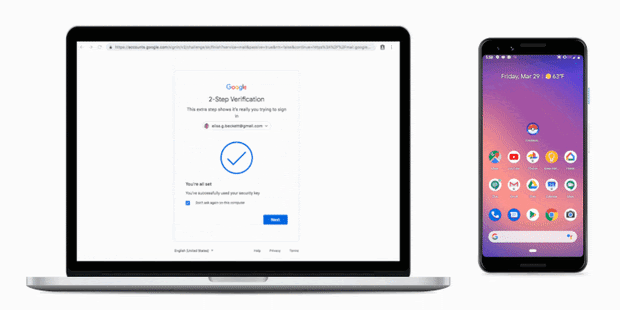
Breaking up the Phishing Attack Chain
Breaking up the Phishing Attack Chain Phishing remains a popular attack method for malicious actors. This attack method is made possible by the wealth of services phishers can purchase on illicit markets: mass mailers, email lists, fake websites etc. Phishing … Read More

The Winners and Losers of the Empire Market Shutdown
The Winners and Losers of the Empire Market Shutdown Empire Market was launched on the dark web in January 2018. By filling the void left by the shutdown of Alphabay and Hansa marketplaces in mid-2017, it grew into one of … Read More

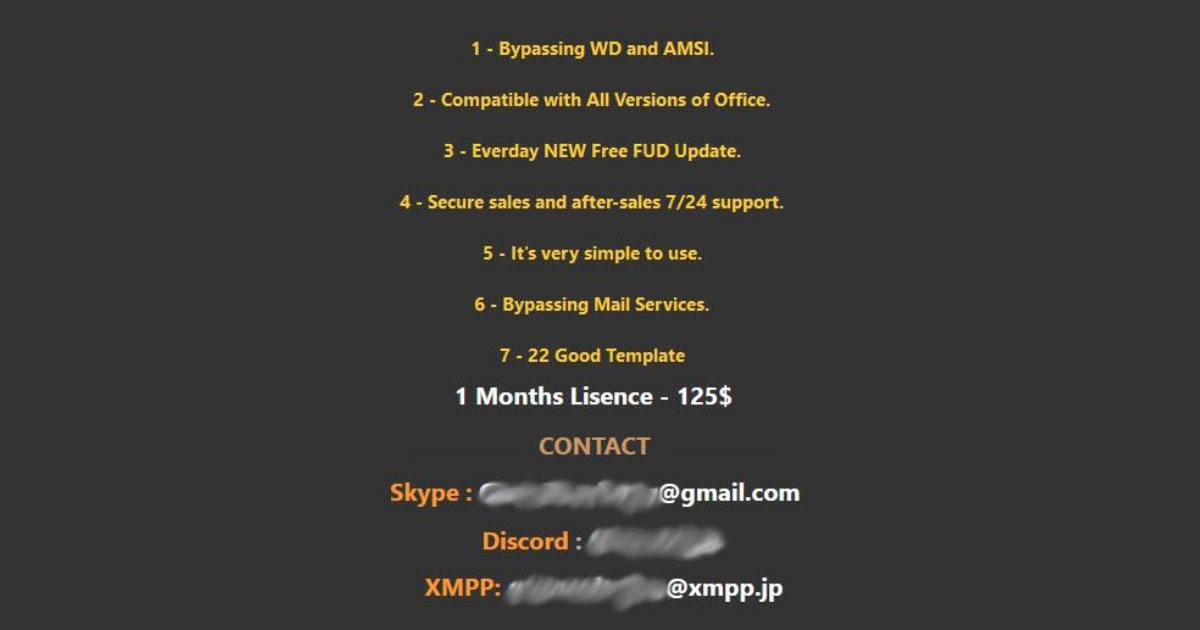
How To Identify The Next Major Cyber Threats through Job Postings
How to Identify the Next Major Cyber Threats Through Job Postings A significant challenge for security teams is to extract intelligence from open-source information. Malicious actors routinely post advertisements like the one below. This actor is offering up a method, … Read More
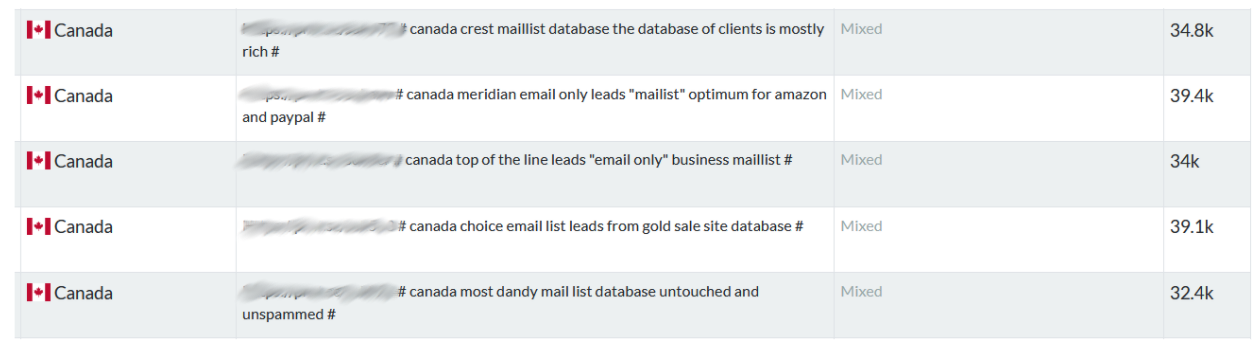
Why all the Spam? How Phishing Emails Get to You
How Phishing Emails Get to You? A phishing attack is any communication (email, SMS, instant messaging) campaign launched by a malicious actor to steal personal data and credentials. Phishing attacks are one of the biggest threats to data security. According … Read More

