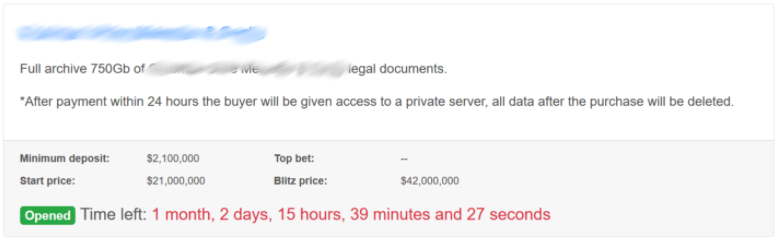
The Low Hanging Fruit: Your Vendors And Partners Ransomware is a growing threat to any organization, government or business. In Canada alone, it is estimated that ransomware attacks and the associated downtime cost our economy CAD$2.4 billion in 2020. HOW … Read More
Digital Risk Protection
5 Trends in Loyalty Program Fraud in Canada
5 Trends in Loyalty Program Fraud in Canada Loyalty programs have grown tremendously in the last decade. Memberships rose to 3.8 billion members recently , with a total value of USD$323 billion for the ecosystem. Loyalty program fraud has significantly … Read More

Preventing Account Takeover in E-Commerce And Retail – August 2020 Webinar Video
Preventing Account Takeover in E-Commerce And Retail Webinar by David Hétu, Flare Systems and Pharid Jaffer Digitalization, cloud based-services, and the rise of online marketplaces and services have increased the number of entry points for malicious actors who want to exploit … Read More
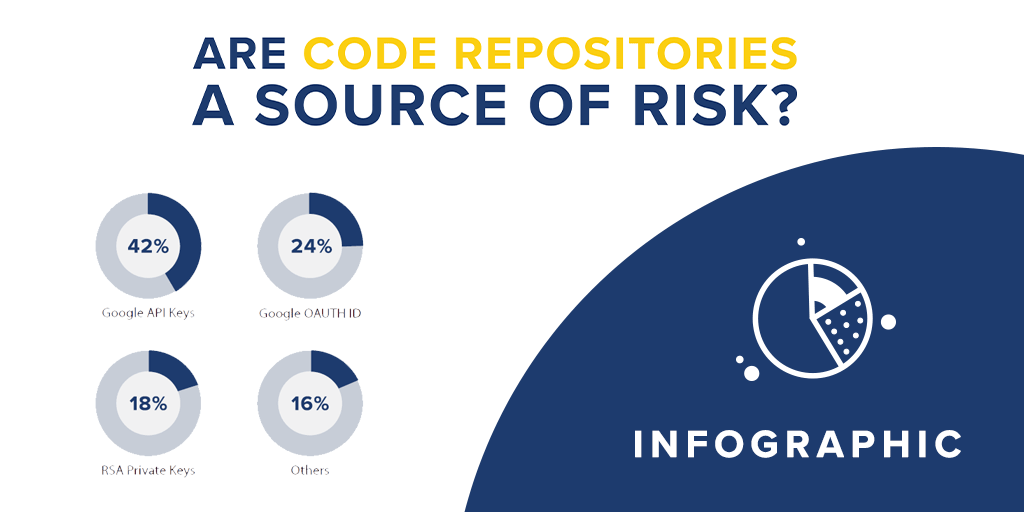
Infographic: Are Code Repositories a Source of Risk?
Are Code Repositories a Source of Risk? This infographic presents the risks your company faces when using code repositories.Passwords and API key leaks lead to loss of data integrity, financial losses, and the risk that even more confidential information subsequently leaks. … Read More

Autopsy of a Ransomware Attack – July 2020 Webinar by Flare Systems and In Fidem
Autopsy of a ransomware attack Webinar by Flare Systems and In Fidem Watch the video! Download the presentation The number and impact of ransomware attacks are constantly increasing. Between 2018 and 2019, the number of attacks has increased by nearly … Read More

Dorking: Preventing Leaks From Hurting Your Firm
Dorking: Preventing Leaks From Hurting Your Firm While readily available, malware is far from being the only tool that malicious actors use to steal data and illegally access computer networks. Malicious actors indeed threaten firms’ security using far more mundane … Read More

How Loyalty Program Fraud Happens
How Loyalty Program Fraud Happens Loyalty programs have grown tremendously in the last decade. Memberships rose from 2.6 billion to 3.8 billion from 2012 to 2016, and are projected to increase to 5.5 billion by the end of the year. … Read More

What Does the “Free” in Free Food Really Mean?
What Does the “Free” in Free Food Really Mean? Hijacked accounts are one of the most common items available for purchase on online illicit markets. On our blog, we’ve discussed in the past the issue of bank credentials being put … Read More

The Risks of Using Corporate Emails for Personal Services
The Risks Of Using Corporate Emails For Personal Services Everyday, Flare Systems collects leaked usernames and passwords on the internet and the darkweb. Our customers use our extensive leaked credentials database to prevent credential stuffing attacks. Credential stuffing happens when … Read More

Do You Speak Fraudster?
Do You Speak Fraudster? To improve our tools and algorithms, part of our daily work at Flare Systems is to read advertisements for illicit goods and services. Our job is to understand who the threat actors are, who they are … Read More