How to decrease false positives when scanning for committed secrets In 2019, some 10 million developers joined Github and contributed over 44 million repositories in that year alone. Github is the most popular code repository, with 80% of its users … Read More
Large enterprise and SMBs

How Do Company Secrets Get Leaked Online?
How Do Company Secrets Get Leaked Online? Back in 2017, Facebook suffered a source code leak, initially believed to have been the result of either a developer intentionally leaking it or a security loophole in company servers. The source code … Read More

How Much Would a Technical Leak Cost You in Stolen Cloud Resources?
How Much Would a Technical Leak Cost You in Stolen Cloud Resources? If you have ever wondered how cryptocurrencies like bitcoin or monero issue new currency, the answer is through a competition called cryptocurrency mining. This competition is open to … Read More

How Sudden Policy Changes Put Company Secrets at Risk
How Sudden Policy Changes Put Company Secrets at Risk Popular among developers, Docker Hub has been used for years to share applications and code libraries. In August 2020, Docker reported its service was used by more than 6.5 million developers … Read More

What is technical leakage and how does it happen?
What is technical leakage and how does it happen? In July, more than 50 international companies suffered a source code leak due to software development misconfigurations in DevOps applications, Bleeping Computer writes. The businesses operated in various industries, including technology, … Read More

Why digital risk protection is vital to protect data privacy in enterprise security
Why digital risk protection is vital to protect data privacy in enterprise security Privacy concerns have lately gained some serious momentum, as Daniel Therrien, Canada’s Privacy Commissioner, has warned that existing laws are behind international standards. This stalling appears to … Read More

Webinar Replay: State of the Cryptomarkets
Winners and Losers From the Shut Down of Empire Market David Hétu, Chief Research Office at Flare Systems investigated and presented the state of the cryptomarkets since one of the biggest illicit market shut down, Empire Market. Replay the webinar … Read More
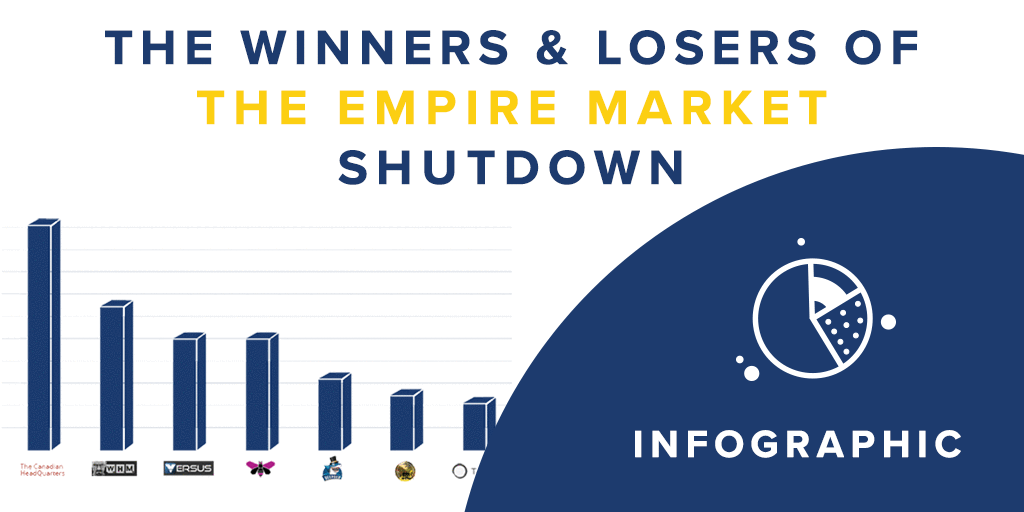
The Winners and Losers of the Empire Market Shutdown
Exit Scam Model of Empire Market In this infographic, we present how the shutdown of the most-trafficked dark web marketplace occured, the aftermath for the malicious actors and what we should expect next from the underground net threats. The exit … Read More
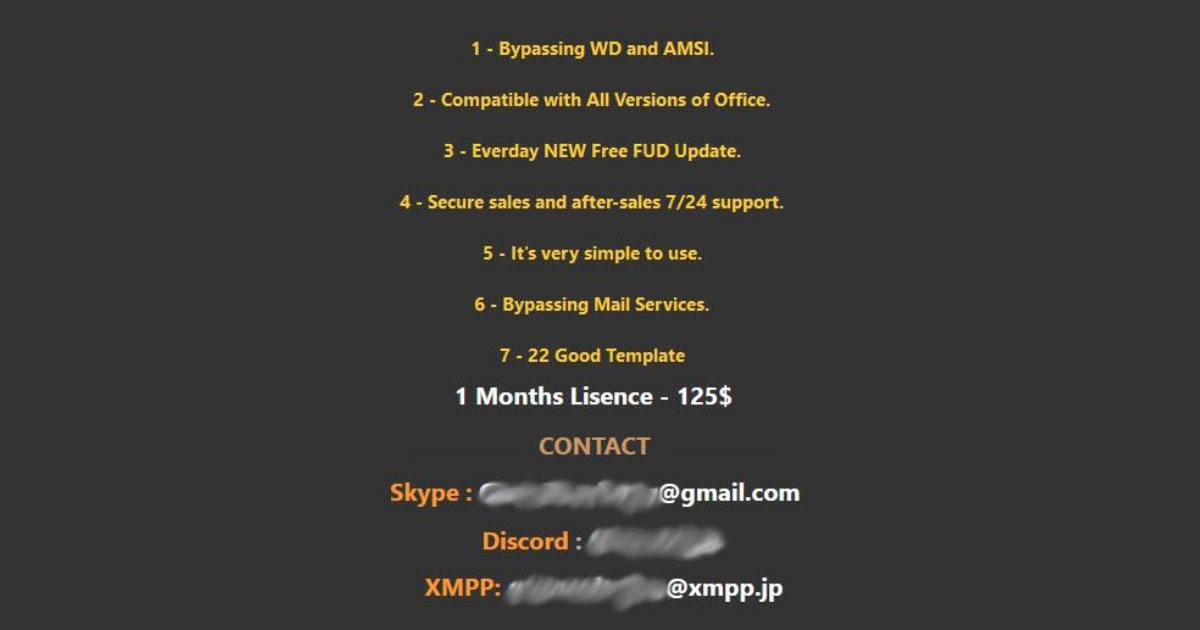
Hacker Contracts: The Economy Behind Illicit Markets
Hacker Contracts: The Economy Behind Illicit Markets Malicious actors often rely on each other to launch attacks. A carding ring that was recently dismantled by Russian authorities, for example, led to the arrest of 25 individuals who were working together. … Read More
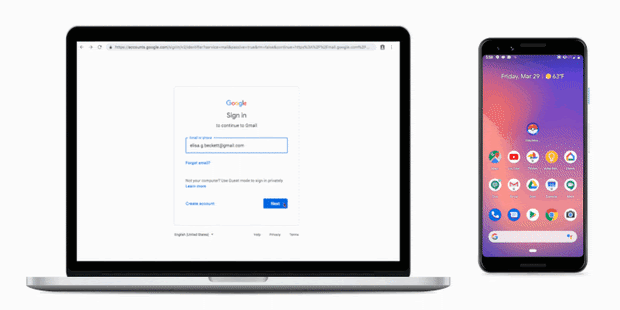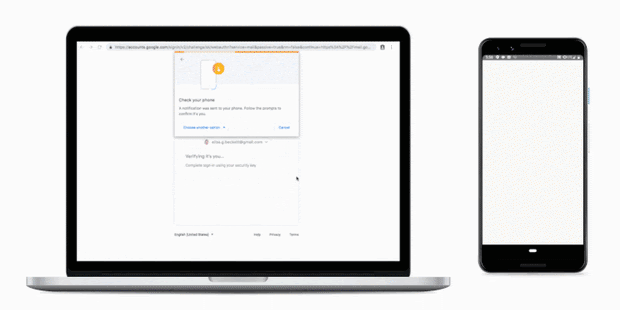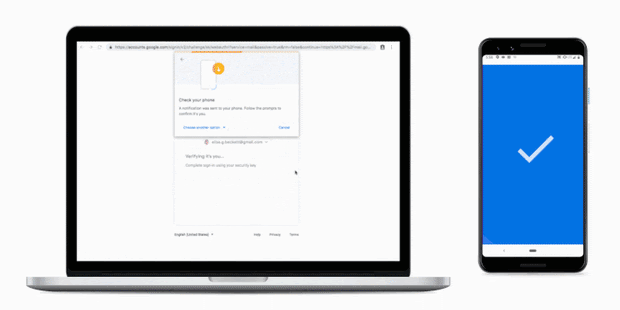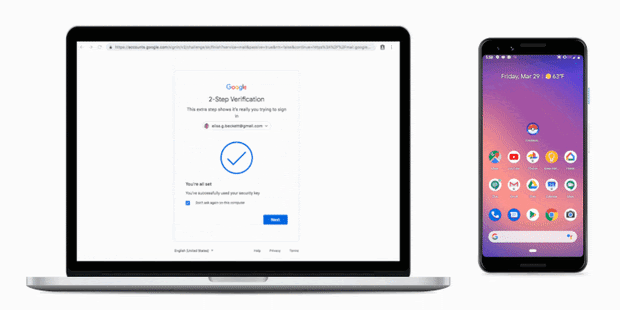
Breaking up the Phishing Attack Chain
Breaking up the Phishing Attack Chain Phishing remains a popular attack method for malicious actors. This attack method is made possible by the wealth of services phishers can purchase on illicit markets: mass mailers, email lists, fake websites etc. Phishing … Read More

