The Winners and Losers of the Empire Market Shutdown Empire Market was launched on the dark web in January 2018. By filling the void left by the shutdown of Alphabay and Hansa marketplaces in mid-2017, it grew into one of … Read More
Large enterprise and SMBs

How To Identify The Next Major Cyber Threats through Job Postings
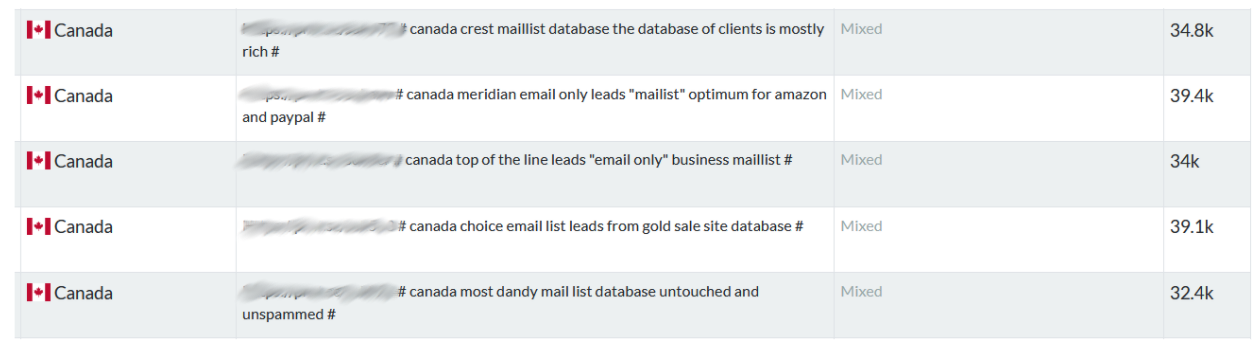
How to Identify the Next Major Cyber Threats Through Job Postings A significant challenge for security teams is to extract intelligence from open-source information. Malicious actors routinely post advertisements like the one below. This actor is offering up a method, … Read More
Why all the Spam? How Phishing Emails Get to You
How Phishing Emails Get to You? A phishing attack is any communication (email, SMS, instant messaging) campaign launched by a malicious actor to steal personal data and credentials. Phishing attacks are one of the biggest threats to data security. According … Read More
Ransomware and Supply Chains
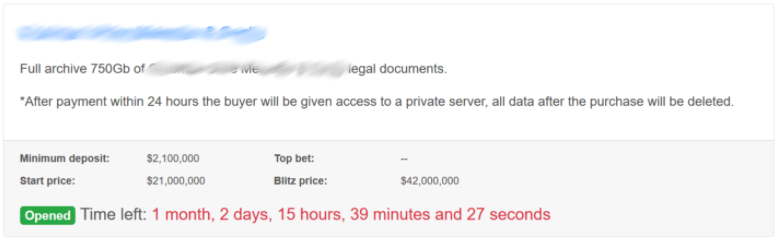
The Low Hanging Fruit: Your Vendors And Partners Ransomware is a growing threat to any organization, government or business. In Canada alone, it is estimated that ransomware attacks and the associated downtime cost our economy CAD$2.4 billion in 2020. HOW … Read More
HOPE Conference 2020 VIDEO: Pricing and Mapping the Underground
Pricing and Mapping the Underground: HOPE 2020 Flare Systems’s David Hétu had the pleasure of speaking at H.O.P.E. (Hackers On Planet Earth) on July 31st this year on pricing and mapping the cybercrime underground. Watch the On-Demand Recording Now! https://youtu.be/OW4a3qldytAHackforums are known … Read More

The Risks of Using Corporate Emails for Personal Services
The Risks Of Using Corporate Emails For Personal Services Everyday, Flare Systems collects leaked usernames and passwords on the internet and the darkweb. Our customers use our extensive leaked credentials database to prevent credential stuffing attacks. Credential stuffing happens when … Read More
What Passwords Do Fraudsters Use?
What Passwords Do Fraudsters Use? Five years ago, Avast published a blog post that analyzed a database of 2,000 passwords used by hackers. It found that hackers use very easy to crack passwords just like most people. In fact, their … Read More

Where Does Stolen Data Go?
Where Does Stolen Data Go? The recent indictment of 4 Chinese nationals gives us an opportunity to talk about a topic that touches all the companies that have had the personal or account information they protect stolen: Where does stolen … Read More

The Truth Behind Joker’s Stash / Wawa Announcement
The Truth Behind Joker’s Stash / Wawa Announcement Over the past two weeks, all the leading news agency have reported that the millions of credit cards stolen at Wawa’s stores in the United States in 2019 have been put on … Read More

Trying Too Hard to Attract Buyers Can Backfire
Trying Too Hard to Attract Buyers Can Backfire Malicious actors face a difficult task in online illicit markets. How can they convince others that they are offering a high quality service (ex. selling stolen credit card numbers) without exposing themselves … Read More

