How Sudden Policy Changes Put Company Secrets at Risk Popular among developers, Docker Hub has been used for years to share applications and code libraries. In August 2020, Docker reported its service was used by more than 6.5 million developers … Read More
Software & Saas

What is technical leakage and how does it happen?
What is technical leakage and how does it happen? In July, more than 50 international companies suffered a source code leak due to software development misconfigurations in DevOps applications, Bleeping Computer writes. The businesses operated in various industries, including technology, … Read More

Dorking: Preventing Leaks From Hurting Your Firm
Dorking: Preventing Leaks From Hurting Your Firm While readily available, malware is far from being the only tool that malicious actors use to steal data and illegally access computer networks. Malicious actors indeed threaten firms’ security using far more mundane … Read More

Exploring Leaked Credentials: Practical Guide To Account Takeovers Prevention – June 2020 Webinar
Exploring Leaked Credentials: Practical Guide To Account Takeovers Prevention Data Security – Threat Intelligence – External Threat Protection Watch the video! As the workplace has moved online and an increasing number of employees begin to work from home, the challenges … Read More

What Does the “Free” in Free Food Really Mean?
What Does the “Free” in Free Food Really Mean? Hijacked accounts are one of the most common items available for purchase on online illicit markets. On our blog, we’ve discussed in the past the issue of bank credentials being put … Read More

The Risks of Using Corporate Emails for Personal Services
The Risks Of Using Corporate Emails For Personal Services Everyday, Flare Systems collects leaked usernames and passwords on the internet and the darkweb. Our customers use our extensive leaked credentials database to prevent credential stuffing attacks. Credential stuffing happens when … Read More
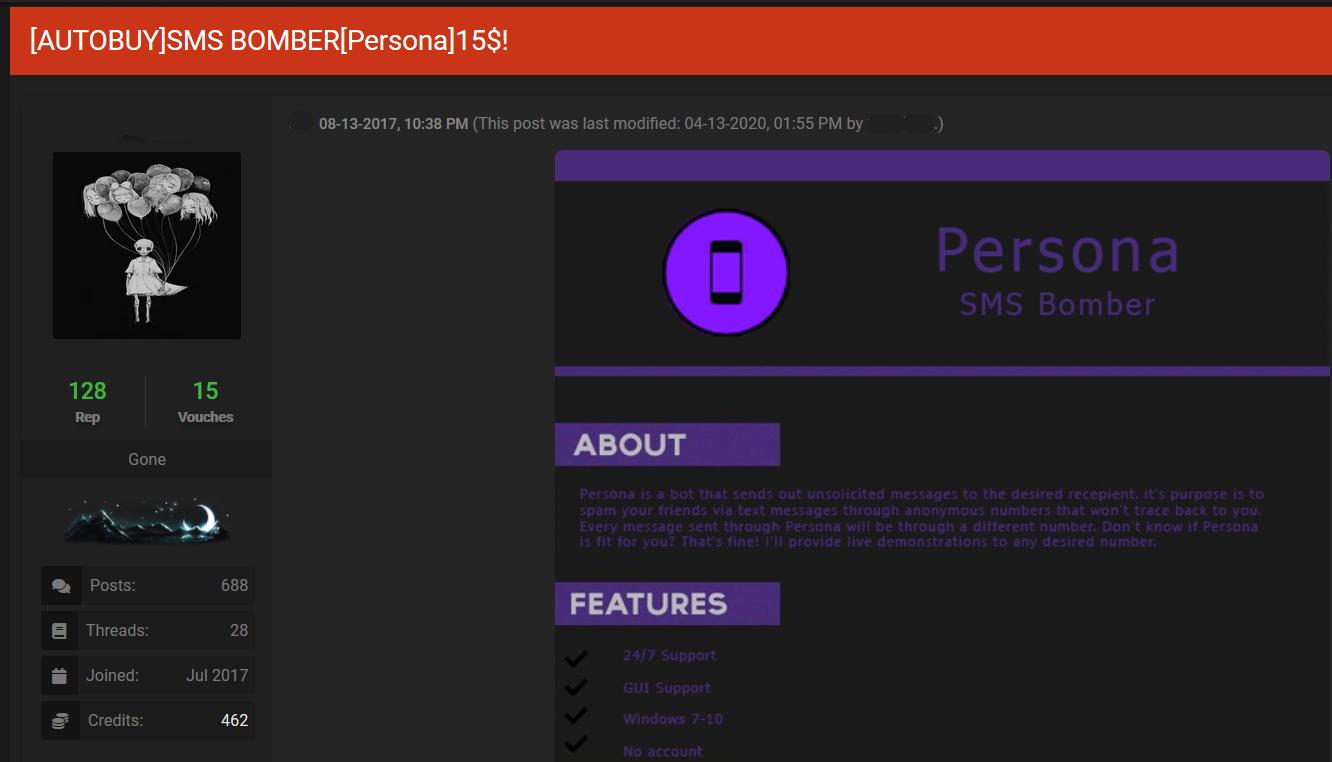
What Passwords Do Fraudsters Use?
What Passwords Do Fraudsters Use? Five years ago, Avast published a blog post that analyzed a database of 2,000 passwords used by hackers. It found that hackers use very easy to crack passwords just like most people. In fact, their … Read More

46M Cracked Passwords – Are People Getting Better at Securing Their Accounts?
46M Cracked Passwords – Are People Getting Better at Securing Their Accounts? A little over a year ago, malicious actors hacked the MyFitnessPal service. With 143 million users, this was one of the largest hack of credentials ever reported. Now, … Read More

